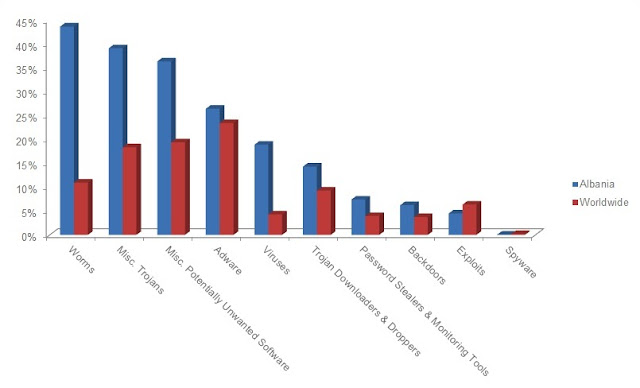
Bugtraq system offers the most comprehensive distribution, optimal, stable and automatic security to date. Bugtraq is a distribution based on the 2.6.38 kernel has a wide range of penetration and forensic tools. Bugtraq can be installed from a Live DVD or USB drive, the distribution is customized to the last package, configured and updated the kernel. The kernel has been patched for better performance to recognize a variety of hardware, including wireless injection patches pentesting that other distributions do not recognize.
Some of the special features that you can appreciate are:
· Administrative improvements of the system for better management of services.
· Expanded the range of recognition for injection wireless drivers.
· Patching the kernel 2.6.38 to recognize 4 gigs of RAM in 32-bit.
· Tools perfectly configured, automated installation scripts and tools like Nessus, OpenVAS, Greenbone, Nod32, Hashcat, Avira, BitDefender, ClamAV, Avast, AVG, etc...
· Unique Scripts from Bugtraq-Team (SVN updates tools, delete tracks, backdoors, Spyder-sql, etc.)
· Stability and performance optimized: Enhanced performance flash and java and start purging unnecessary services. So that the user can use only the services you really want.
· It has incorporated the creation of the user in the installation, which is created with all system configurations.
· We are the distribution and Forensic Pentesting with more tools built and functional, well organized menu without repetition of the same to avoid overwhelming the user.